


Link here> https://academy.hackthebox.com/preview/certifications/htb-certified-defensive-security-analyst
According to Discord, I am one of about 400+ CDSAs globally. That makes me pretty cool I guess? I also ordered the certification package which consists of a T-Shirt and the cert itself (still shipping over).
But enough said. Is this a cert that is bang for your buck in this terrible economy?
All ratings are out of five star.
Overall Rating – ⭐⭐⭐⭐ (Take the damn course)
HR Value – ⭐
Course – ⭐⭐⭐⭐
Exam – ⭐⭐⭐⭐
Value for Money – ⭐⭐⭐⭐ ( would have been an easy five star if it had any HR Value!)
The CDSA provides exceptional learning value for its cost (US$250 for the exam, and the course itself could be as cheap as US$8/month if you have a student account). You also get to keep the course material even after your subscription expires. The exam itself is challenging yet fair as it tests your understanding of the materials through two practical scenarios over seven days which includes writing a comprehensive report.
The downsides are that (i) HTB exams remain unrecognized by HR and CDSA being one of the new kids on the block is no exception; (ii) one has to complete the extensive SOC Analyst path before being allowed to attempt the exam ; and (iii) the labs in the path are not very stable and can lead to a fair bit of frustration. I had to rush through the last few modules so that I could take the exam before my voucher expired. The SOC Analyst path can take quite a chunk of your time and this may not work for everyone. That said, the SOC Analyst is well worth taking even without taking the CDSA exam.
Yea basically buy it if you want to learn but don’t expect it to get you a job.
The CDSA has to be reviewed together with its accompanying (and mandatory) SOC Analyst Path. This is because completing the 15 modules in the Path is required before you are allowed to attempt the CDSA exam.
There is A LOT OF MEAT in this path. Not all the modules are equally long. Some like the “Incident Handling Process” and “Security Incident Reporting” are fairly short, needing maybe an hour of your time at most while others like “Windows Attack and Defense” are huge sections by their own. I took about three months on and off to do the path though I only really started to grind the path in the month leading up to my subscription expiry.
It covers a wide array of topics from SIEM, to Memory forensics to common AD Attacks and detection. From this course, you can expect to learn the following:
Lets go through the modules and my thoughts on them one by one:
Rating: 3/5
Time Investment: 1 to 3 hours?
A theoretical and introductory module to the various steps in the Incident Handling Process. Labs are simple and each lesson is short. I guess it gets the job done. Just theory. Nothing too exciting here.
Rating: 4/5
Time Investment: At least 6 hours
Here is where it starts to get fun. You are introduced to the Elastic Stack, its use cases and how to construct Kibana Query Language (KQL). At the same time though, you will start to experience the “Verboseness” of HTB modules. Depending on your patience, you will either see it as detailed and informative or long-winded. This module is fairly long with hands-on exercises where you are taught how to craft simple KQL queries to investigate incidents like multiple failed logins. I thought as someone new to KQL that this was a good module to get your hands wet with Elastic.
IMO, I feel that the sections on the MITRE ATT&CK framework and an overview of the SOC are out of place here but they are fairly short and theoretical. Also this module will likely be one’s first touchpoint with the VMs in this path and unfortunately, I find the VMs to be rather laggy and unstable. This would be one of my biggest bugbear with the path itself (the exam environment is pretty good though).
Rating: 3.5/5
Time Investment: Around 2 to 3 hours
Mini-Module is a suitable description for this. There are only a few sections here as this largely deals with manual parsing of WinEvent logs either through the Event Viewer or using Powershell’s Get-WinEvt. I also learnt something new with Event Tracing for Windows though I left not quite knowing how to best use it.
This module also provides a whole laundry list of Event IDs that are usually referred to when triaging an incident so ahem take note. I will probably refer to this if I ever do a SOC or DFIR role.
No sane person will parse logs through the event viewer so this is just to tell you that it can be done.
What I do like about this module (and subsequent modules) are introductions to attacks/threats that I certainly did not expect to find in a blue team course and so early on in the path. I refer specifically to “Detecting Unmanaged PowerShell/C-Sharp Injection”. This was something that was new to me and it was an eye opener and tells me that HTB is serious about providing you with knowledge.
Rating: 3.5/5
Time Investment: Around 2 to 3 hours
Another Mini module. Some theoretical introduction to Threat Hunting and CTI. Not a super fan of the theory parts but at least they are kinda short.
The fun part was the practical portion where you are given an example of Threat Hunting using Elastic and the methodology to step through the process after receiving information from the CTI team. I like that each step is well explained with accompanying screenshots. Take many notes here. Wish there was a few more examples though!
Rating: 4.5/5
Time Investment: 3 to 4 hours?
I like this module. Introduces you to Splunk, how to ingest logs and then walks you through step by step through a few scenarios. You then get to practice constructing queries. Does it job well. No complains. I was deliberating over giving it a perfect score but decide to dock 0.5 star because the next module is fully deserving of a perfect score.
Rating: 5/5 🚀
Time Investment: 12 hours or more?
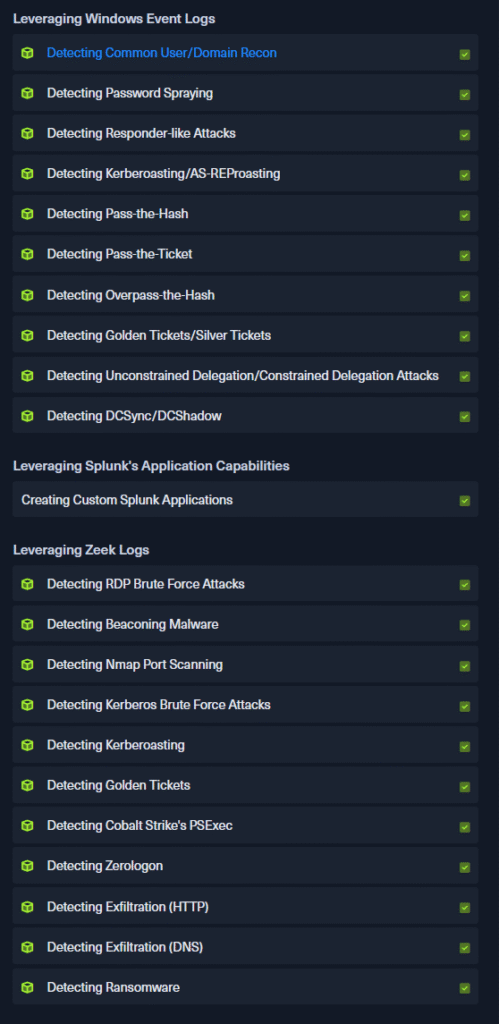
You know this module is cooking when this is the only module that is marked as Purple. If you have no experience with AD or pentesting, this module could be very rough because it dives fairly deep into the weeds of AD. It was fairly accessible to me because I had prior knowledge of the attack paths. If not, you will have to spend quite a bit of time on this module and consulting good ole google to understand more about what’s going on. I mean just look at what is being covered:
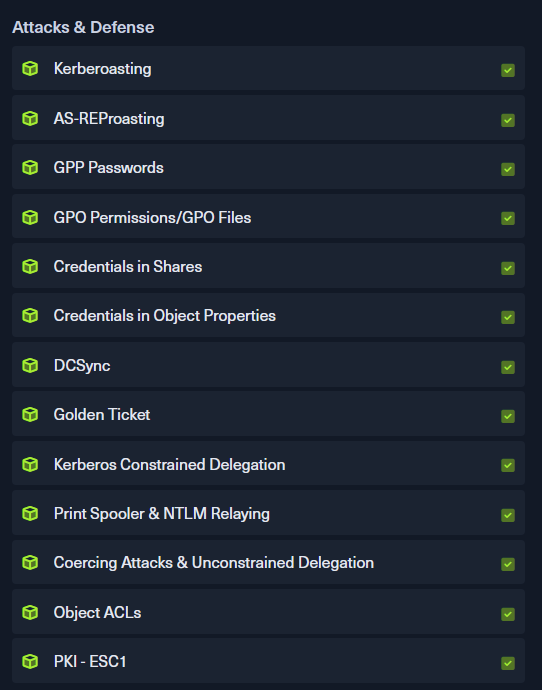
This is a phenomenal module. You learn how the above AD attacks are carried out and then you learn how to detect them. As someone with the PNPT and the OSCP+, I was learning a ton of things from this module from the attack angle and intrigued by the number of artifacts and logs that we are triggering from these attacks. You will be looking at the consequences of these actions on the hosts and the kind of Windows Event ID and Sysmon logs that are generated by these. You have to experience this for yourself. Very heavy module but so worth it.
Rating: 4/5
Time Investment: Around 3-5 hours?
You will be introduced first to the TCP/IP model and then using both Tcpdump and Wireshark to analyse packets. I find the modules to be fairly comprehensive so no complains here. Does its job.
If you need more practice, https://www.malware-traffic-analysis.net/ is a great site with its own guide on how to really git gud at using Wireshark to analyse packet captures.
Rating: 4/5
Time Investment: At least 4 hours
Not sure why the difficulty is Easy when compared to the previous module. In here, you learn how to use Wireshark to detect more “sophisticated” threats such as ARP spoofing and DNS tunneling. Quite a fair bit of learning value so yet another good module.
Rating: 3/5
Time Investment: Around two to four hours
I did find this module to be a bit on the boring side. You are taught fundamentals of Suricata, snort and zeek and how to configure and write some simple rules for IDS/IPS. Just not my cup of tea unfortunately. I might have just auto-piloted through without really learning…
Rating: 4/5
Time Investment: Around 12 hours or more
The only rated HARD module in the Path. For good reason. Malware analysis is usually an advanced topic especially when you have to go into debuggers and disassemblers which this module covers. It does a fairly decent job at introducing static analysis on both Windows and Linux platforms though i find the dynamic analysis portion to be a bit short as it only had one section and one example.
The real difficult part is the Code Analysis section where you disassemble and debug a malware sample. Whew, this is where you are likely to spend the majority of your time in this module. I would say HTB did its best to try to demystify this part. It will be a module that I will need to refer back from time to time.
Rating: 2/5
Time Investment: Around 2 to 4 hours
IMO, i personally felt that this module didn’t quite belong to this path. It teaches you obfuscation techniques used by attackers and how to decode them but there is no obvious link back to the modules that we have been doing which has mostly revolved around detecting threats or learning how to use blue team tools. Didn’t like this module. At least it was short
Rating: 4/5
Time Investment: Around four hours
The bread and butter. This module is good because it explains what YARA and Sigma are, how to write them and provides plenty of opportunities for you to practice. Nuff said.
Rating: 4/5
Time Investment: Around six hours
This only covers Windows btw. For what it is worth, I thought HTB managed to cover a lot of ground in this module, from teaching how to capture disk and memory forensics to analyzing them. There are also adequate amount of practice opportunities. I learnt new things such as KAPE and Eric Zimmerman’s suite of tools which helped enhanced my knowledge pool. Great module.
Rating: 5/5🚀
Time Investment: around 8 hours or more
Awesome for the same reason as module 6. The whole module is practice against the various scenarios using Splunk. I love modules that let you practice. Perfect module. Check out the sections below
Rating: 3/5
Time Investment: Around two hours
Lots of theory and stuff on how to write a report. Super useful if you are taking the CSDA exam as you will be referring to this module A LOT as you write your exam report. Otherwise, good read but nothing too special.
Now that you spent at least a month (likely more) of your life grinding that SOC Analyst path to completion, you earn the rights to take the exam!
Lets talk more about the structure of the exam before we move on
You can start the exam at any time once you have completed the SOC Analyst path.
Each exam voucher entitles you to two tries. If you fail but submit a report, you will (supposedly) get feedback from the examiner on how to do better. (I passed on my first try)
You have seven full days to attempt the exam. This includes report writing as well!
You will be provided a VM. All you need is something like openvpn and any tool that allows you to RDP into the VM so you dont have to worry about creating a VM specially for this exam.
Everything in the SOC Analyst path is in scope.
Free to use google and any online resources for reference (very important!)
I am an example of WHAT NOT TO DO when taking the CDSA exam. I am personally a bit surprised that I passed but to be fair, I did put in tremendous work and dedication during that seven days!
Here is what I did and WHAT YOU SHOULD NOT DO:
Advice 1

Advice 2

Advice 3
From my ill preparedness, I still managed to pass the exam. So what are my thoughts (and tips)?
I would love to talk more about the exam because I genuinely had a lot of fun and learnt plenty over the course of the seven days but I am going to err on the side on the caution and share the above for now.
Give it a shot if you have the time (and the budget). I think HTB has created a very good intermediate level Blue Team cert and I hope to see it recognised in the future!
With that signing off:)