


All answers are base-64 encoded to avoid spoilers:)
Dark Waters is from an OSINT training company called Kase Scenarios. You can browse through their catalogue here! https://kasescenarios.com/osint-training/
Welcome to Dark Waters, a scenario that allows you to take on the role of Investigative Journalist Alec Wolfe as he uncovers deadly secrets about a small town in Pennsylvania.
Alec receives a letter from someone called P. The letter states “Everything is not what it seems in Glen Rock, Pennsylvania, Test the water.”
Off we go to Glen Rock as Alec.
I am using Maltego to populate my data points and see if link analysis can help me uncover any threads.
Q1: What is the name of the protestor’s relative that was the first to own land on what is now Glen Rock?
A: We received the following information from the protester:
We used the Google search engine with the following search terms
glenrock pennsylvania 1837One of the top results lead to this website https://www.glenrockpa.org/news-info-faq/history/ which on the surface appears to be a website providing information about the town.
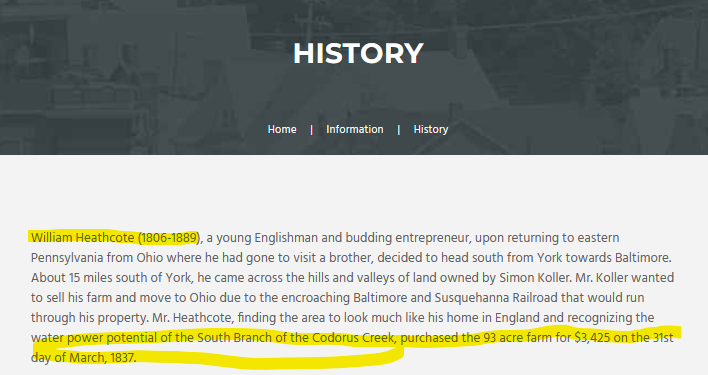
ANSWER
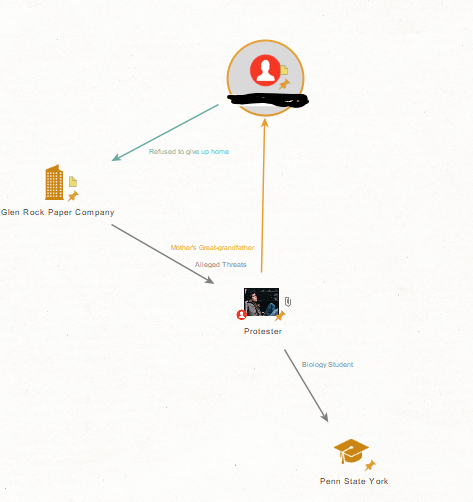
V2lsbGlhbSBIZWF0aGNvdGU=Our current Maltego graph looks like this (not including Lisa and the Person “P”)
Q2: What is the name of the main Railroad through town?
On google, the following search terms contain multiple references to a certain railway
glen rock pa railroadWe find the following article at https://www.northerncentralrailway.com/glen-rock/ with the following excerpt
What we now know as the town of Glen Rock, was originally a farm owned by Simon Koller. Mr. Koller was not interested in the railroad running through his property, so it was sold to William Heathcote, who developed the settlement into the second most industrial city in the county. The settlement was originally called Heathcote’s Station, but when the town was incorporated in 1859, the name was finalized as Glen Rock.
Answer:
Tm9ydGhlcm4gQ2VudHJhbCBSYWlsd2F5Q3: On the side of the local library, what does the third part of the mural say?
Glenrock is a fairly small town (less than 1km by 1km according to google map) so there might be even only one library. Hence we hop to google, locate Glen Rock PA and then search the area for library. As expected, only one result was returned; Arthur Hufnagel Public Library of Glen Rock
Using Street View, we locate the murals at the side but we are not able to zoom in enough to see any words.
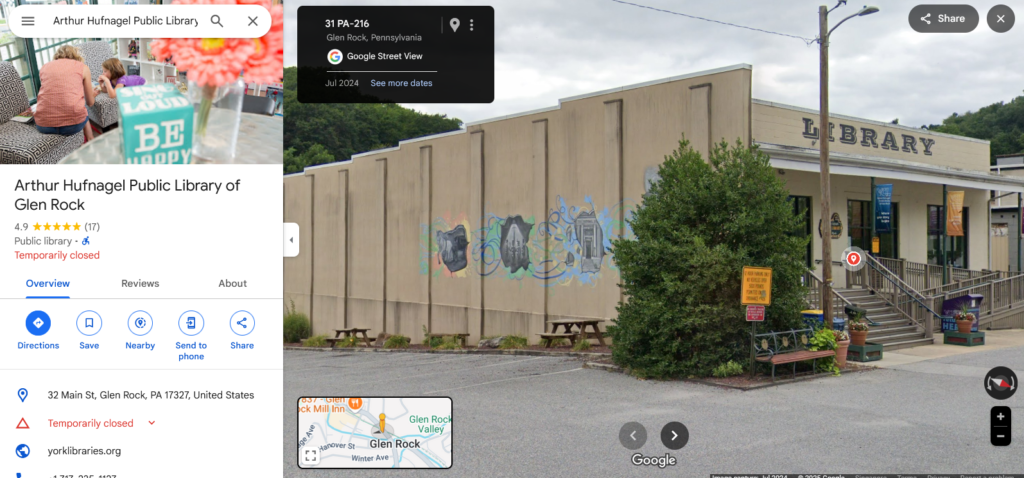
We then pivoted to the photos that are tagged to the location and we find a much clearer shot of the murals that revealed the words on the third part of the mural

Answer
Rmlyc3QgTmF0aW9uYWwgQmFuaw==Q4: Which female artist donated her pastel work “under the rainbow” to the library?
We googled using the following terms and come across an issuu article (including the full name of the library does not seem to return any results so I decided to just reduce it to Public Library of Glen Rock)
The article is here https://issuu.com/engleprintingandpublishing/docs/ccs_102319. We are able to use the search feature and searched for “under the rainbow”.
"Public Library of Glen Rock" "under the rainbow"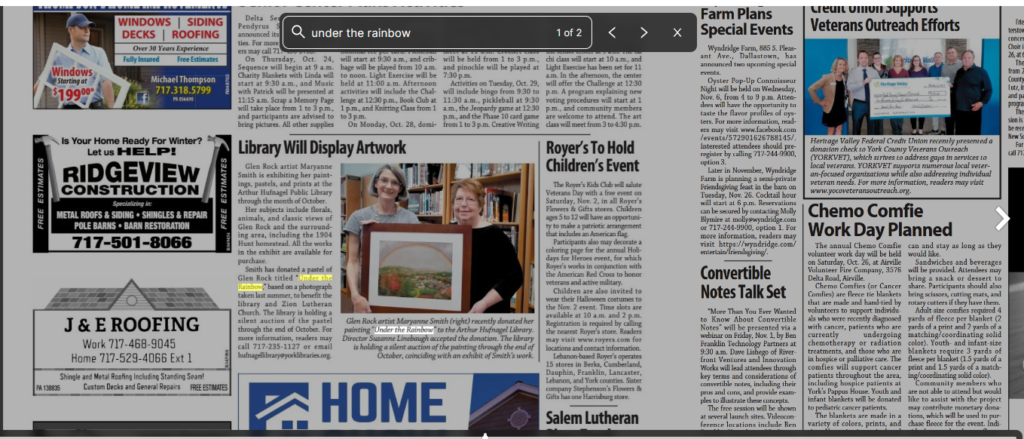
Answer
TWFyeWFubmUgU21pdGg=Q5: What is the street name of Maryanne’s studio?
With the full name and the town’s name, a simple search with the terms below
maryanne smith glen rockrevealed multiple links to an auction website (https://www.onlinehuntingauctions.com/SLA-55-Altay-Argali-Painting-by-Maryanne-Smith_i35406483) where Maryanne’s artwork was being auctioned. The auction page reveals the studio’s name as well as the full address and contact.

The answer is a little tricky but after a few permutations of the street name, what worked was below (My feedback to Kase would be to define the answer syntax in this case <name> Street without any number prefix)
Um9uYWxkIFN0cmVldA==Q6: Where was this taken in town?

We are given a picture and we know that this is somewhere in Glen Rock.
While image metadata could be possible, in this case, there does not appear to be any metadata. The next step is a reverse image search. Nowsaday, there is some AI interpretation when doing google search but we still need to validate the results. It references a place called Ruins Park in Glen Rock so lets see if we can find this place.
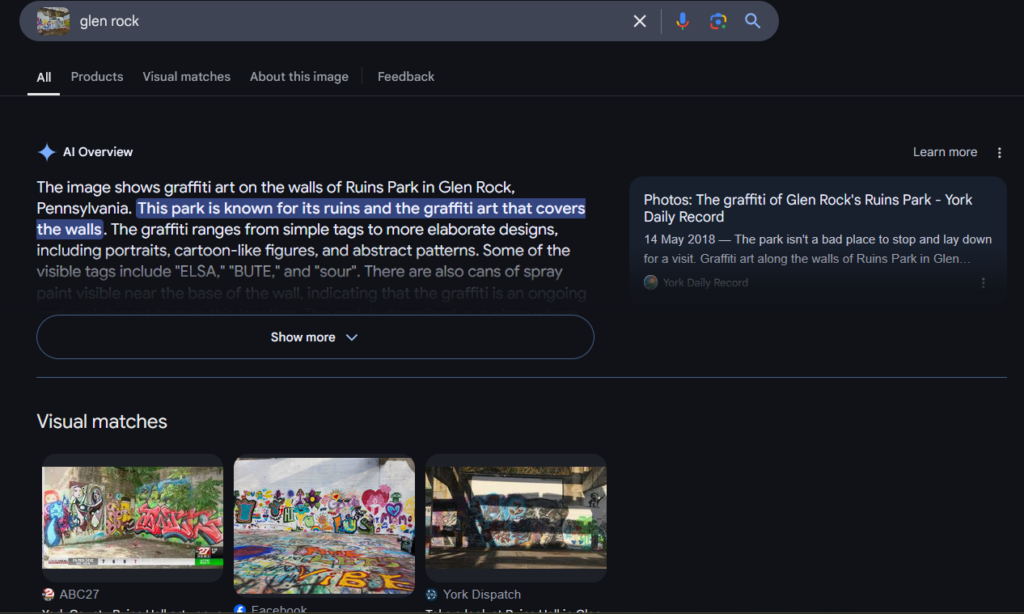
We use the Google Street View feature to explore Ruins Hall and we find what appears to be the spot where the above picture was taken though part of the graffiti has been painted over. We can still see the two female heads that was present in the photo and the location seems to match.

Answer:
UnVpbnMgSGFsbA==Q7: The protester was attending an event there on June 8th 2018 what was it?
Use the following search term on Google
"Ruins Hall" Glen Rock June 2018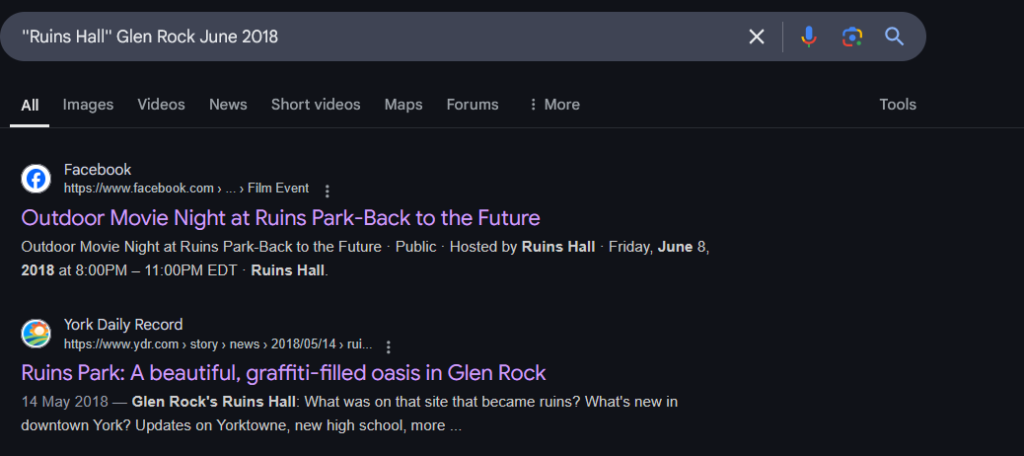
Answer
T3V0ZG9vciBNb3ZpZSBOaWdodA==
Q8: Which movie was shown at the event?
Answer:
YmFjayB0byB0aGUgZnV0dXJlQ9: What was the high temp on that day in Celsius(Only one decimal point is needed)
Google search the following terms (8 june 2018 glen rock pa temperature) and go to this result, adjust the date to 8 June 2018 to see the high temperature in Fahrenheit (https://www.wunderground.com/history/daily/us/pa/glen-rock/KMDT/date/2018-6-8). Convert to Celsius using google.
Answer:
MjcuNw==Q1:Who created this flyer?
We were able to download the flyer. We could use exiftool or just right click on the file and check the properties. We see a name inside the author field.
cGF0dGkgc3RhbnRvbg==
Q2: What is Patti’s favorite thing to do?
I wasn’t sure if Kase had created fictitious social media accounts for Patti but off to the Google Search Engine with the following terms:
"Patti Stanton" "Glen rock"We actually find the GRPC’s website (hosted on kasescenarios) with details about Patti. We also find other employees of GRPC which could then add to our maltego graph

Answer
c3RheWNhdGlvbnM=The maltego chart as of now
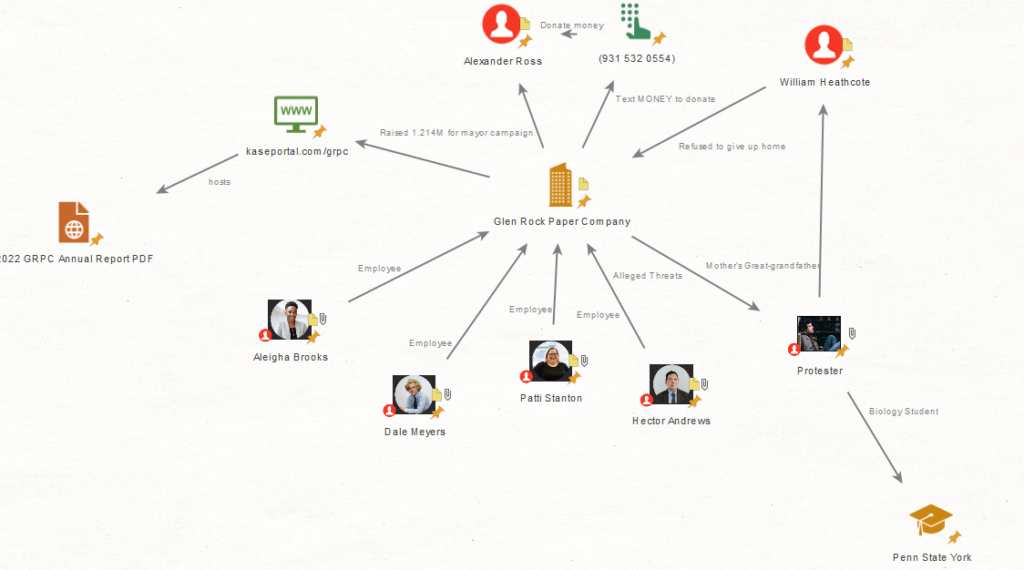
Q3: What is Patti’s home SSID?
An SSID (service set identifier) is a sequence of characters that uniquely names a Wi-Fi network.
For SSID, the go to tool is WiGLE. However I had issues with registering so I can’t really do this exercise (and the subsequent questions). Without registering and logging in, you cant see details. We can assess that Patti stays in Glen Rock, PA so we can narrow the search area of WiGLE to Glen Rock and then we could even filter the year since she has worked with GRPC for the last two years.
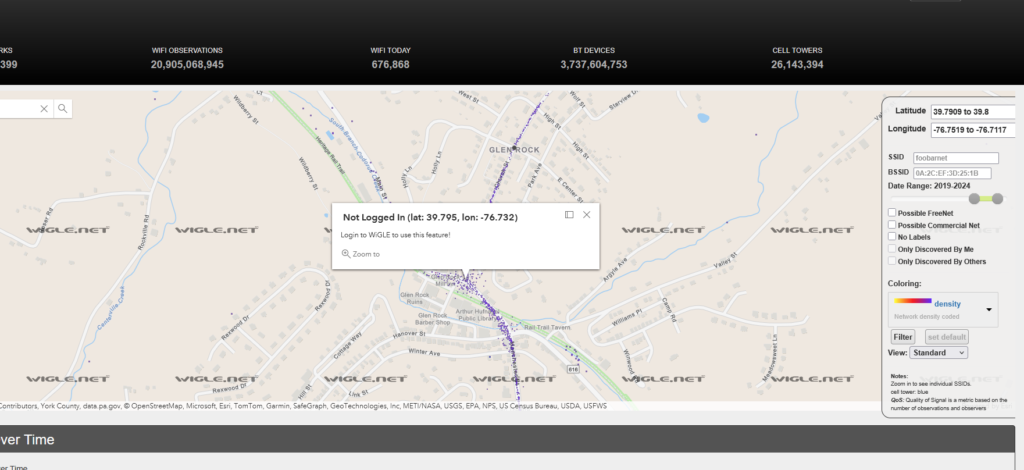
I referenced another walkthrough by https://thefish.nz/2023/dark-waters-write-up/
Answer:
U3RheWNhdGlvbiBXaUZJQ4: What is the BSSID?
If you had the previous answer you will probably have this as well.
M0M6N0E6OEE6OTM6RDI6NUU=Q5: What year was this BSSID first seen?
M0M6N0E6OEE6OTM6RDI6NUU=Q6: Who is the vendor of this device?
To find out the vendor, we take the first three octets of the BSSID. In a sense, it is a similar concept to MAC address vendor lookup.
QXJyaXMgR3JvdXAsIEluYw==Q7: What is the parent company of Arris Group Inc?
Finally, I am free of WiGLE and can once again play along. However this is actually kinda tricky. A google search for “Arris Group Inc” shows that it has been bought over by CommScope in 2019 so surely the parent company is CommScope? However it isn’t so honestly I was a bit baffled.
A discord hint suggest using opencorporates which is a good resource for company OSINT information. Searching for Arris Group Inc reveals a link in which we can see the parent company
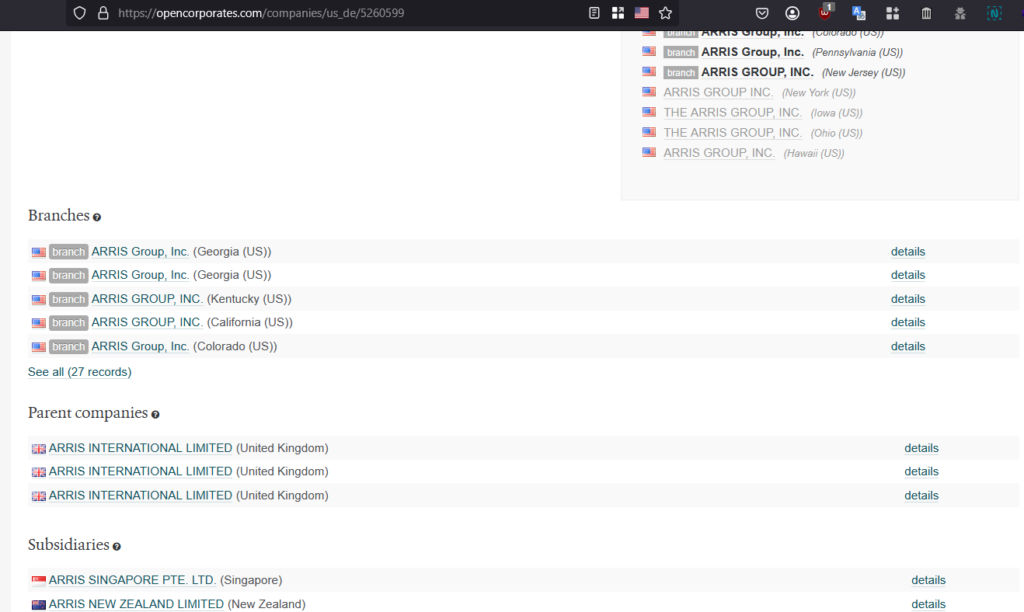
Subsequently adding the “parent company” search term to “Arris Group Inc” on google search reveals this article (https://www.commscope.com/press-releases/2016/arris-completes-pace-acquisition/)

It differs from the above answer but I did not check if this other answer will work as well.
Answer
QXJyaXMgSW50ZXJuYXRpb25hbCBMaW1pdGVkTried to crash the party but was denied.
Q1:How much money has GRPC donated to Alexander Ross?
We noted this when examining the company website.

Answer
MTIxNDAwMA==
Q2: What is the GRPC campaign phone number for Alexander Ross?
We find this info on the GRPC website
Answer
KDkzMSkgNTMyLTA1NTQ=Q3: How much did Glen Rock Paper Company spend on PR services in 2022?
On the website itself, there is a company annual report for 2022 so that is likely where we can find the information.
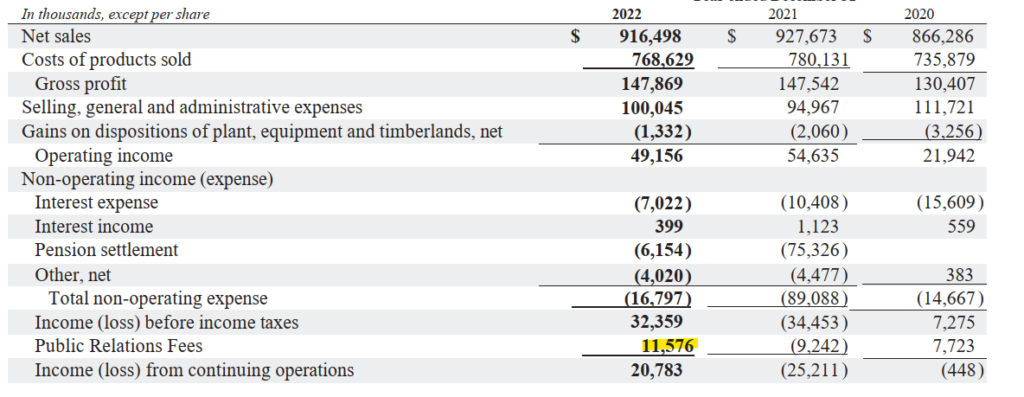
The answer appears to be an oversight. The table states that the values are in thousands but putting in 11576000 is wrong but 11576 is correct.
Answer
MTE1NzY=The plot thickens. P may be Lisa’s brother, Peter who was found dead two weeks ago. Peter was apparently investigating GRPC and was convinced of a conspiracy that led to his daughter, Elizabeth’s death.
A mysterious email impersonating Alec (rockthesocks1982@fastmail.com) was sent to the Lab to cancel the analysis order of Alec’s water sample.
Q1: What is the full name of the owner of this email address?
With an email address, I checked the following in sequence:
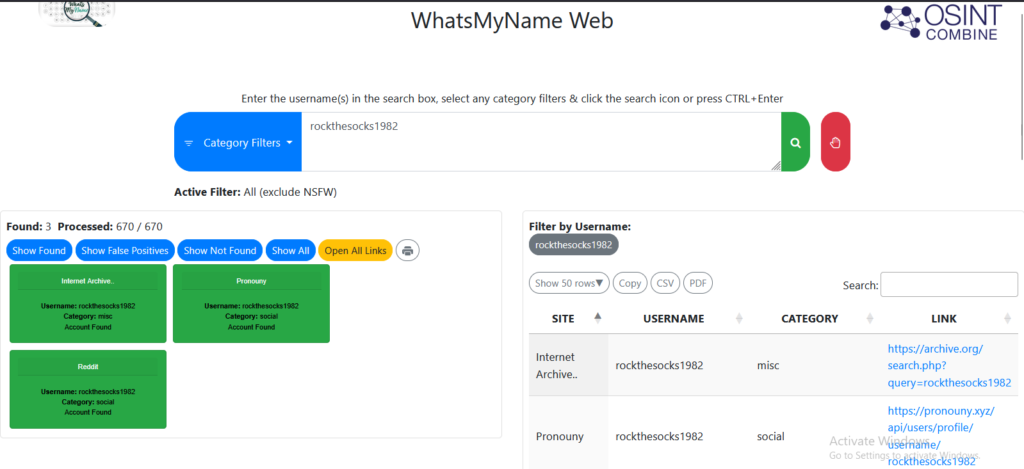
However it seems that the comments were deleted which made me a bit suspicious on whether this was a rabbit hole and an actual user.
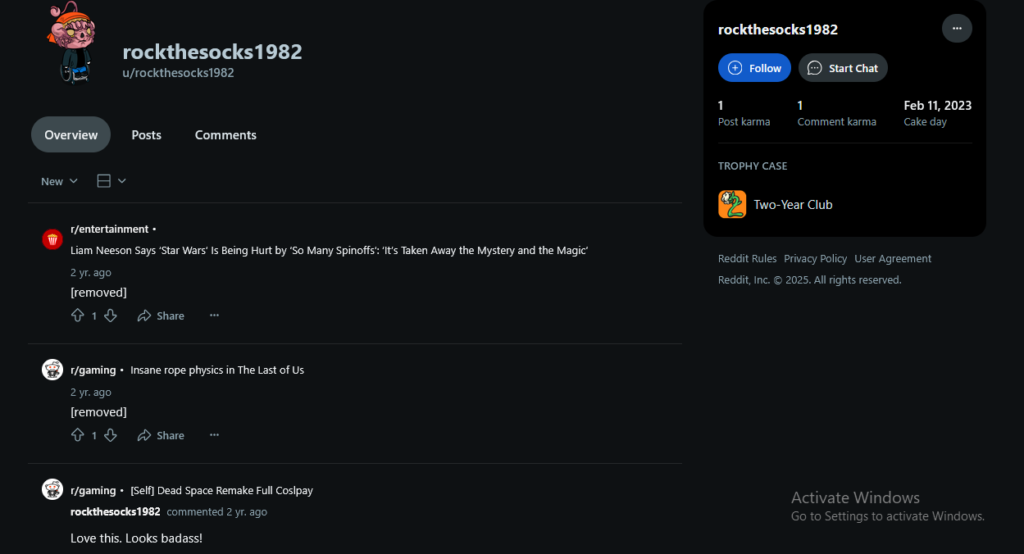
I then used wayback machine to see if there is an archive of the Reddit account and I was able to find an “image” taken of the account on 20 July 2023. We then pivoted on the steam account link to see what we can find out.
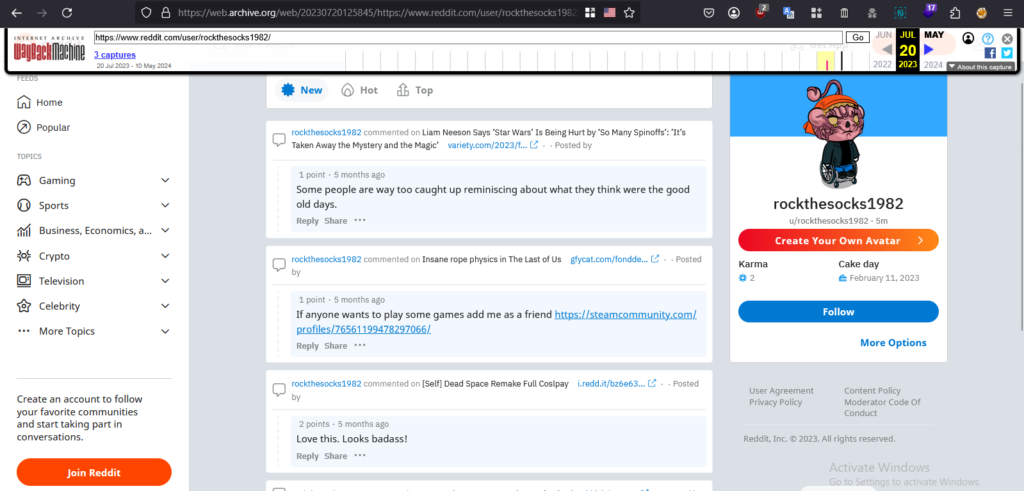
Interesting. This might be our target as the State (Pennsylvania) is relevant. We see 1982 used often which could be the person’s birth year. More importantly it appears that there is a potential name “butch cassidy” which we can pivot from (which doesnt do anything unfortunately). We do get a bunch of alias that we can tag to this person. (off to Maltego!) Before that, I googled to see if there were any Steam ID osint tools and there were!
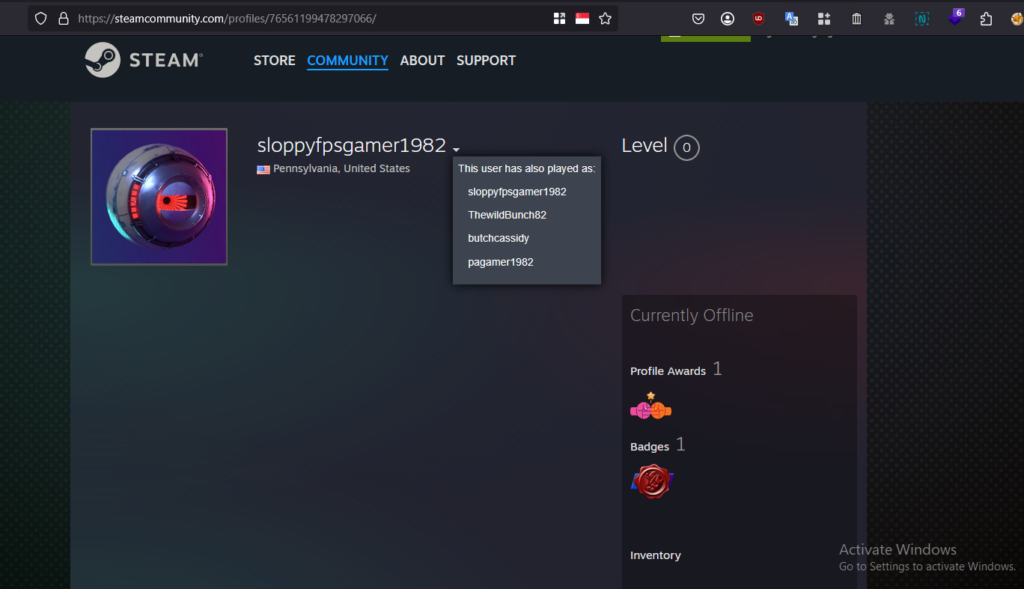
This webpage (https://ohshint.gitbook.io/oh-shint-its-a-blog/osint-web-resources/gaming) suggested a few tools that we can use. Using findsteamid.com, we were able to extract the Real name? associated with the steam profile. John B.
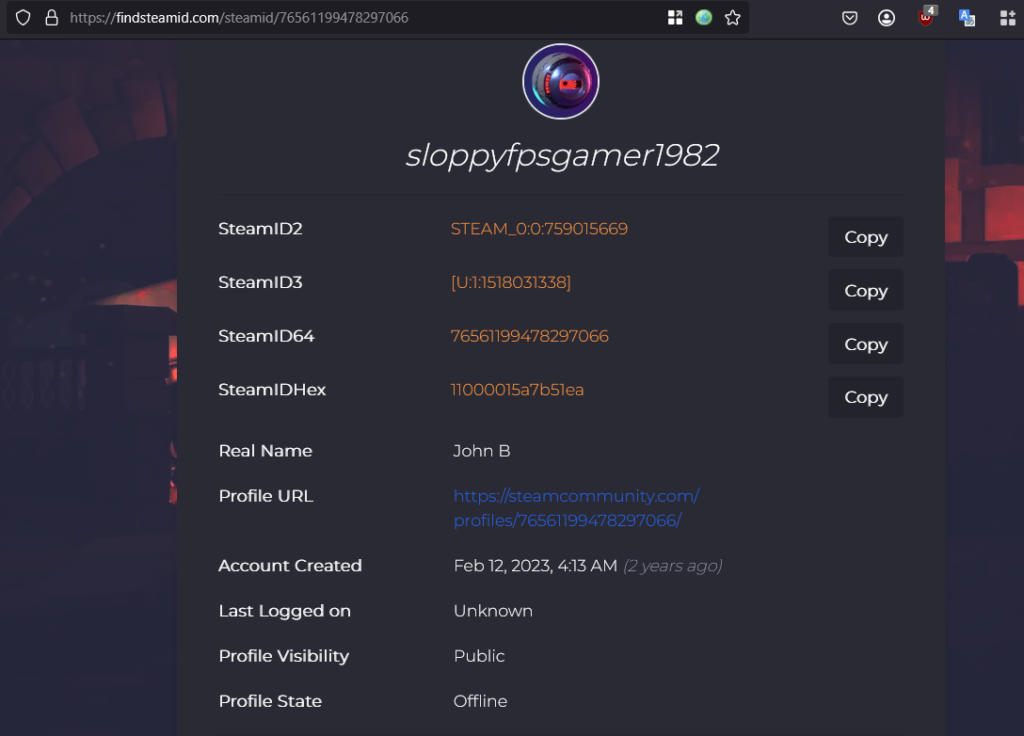
Not much to go on but lets see if we google John B and say Glen Rock (safe to assume that this person is in Glen Rock), but did not see any good results. I then pivoted to social media and see what I can find. On facebook search, I used the filters to narrow down John B living in Glen Rock, PA but still fairly substantial results. Time to brute force and look through each profile.
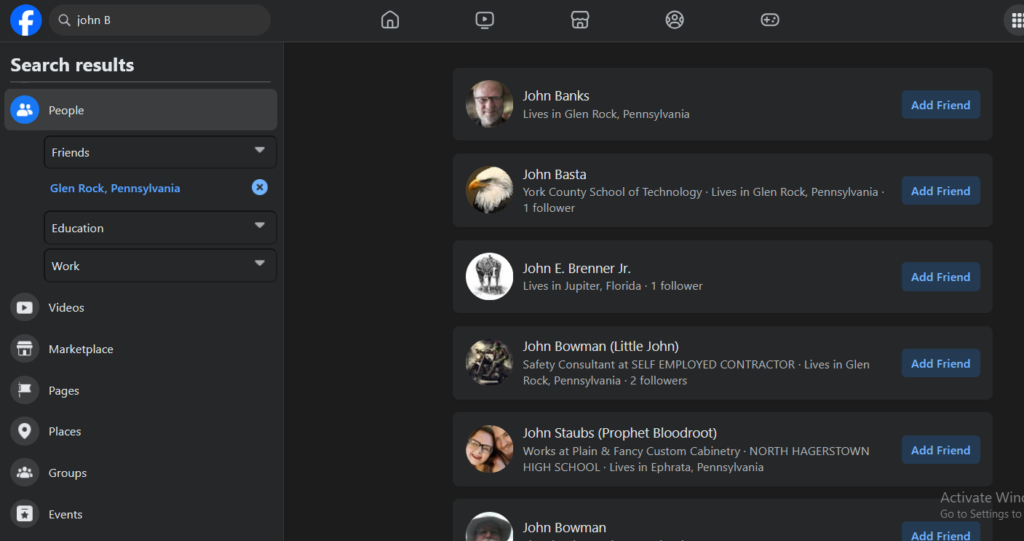
By some stroke of luck, it appears that John Banks is likely the person behind the email when we examine his posts. Behold. Plenty of new information for my maltego collection.
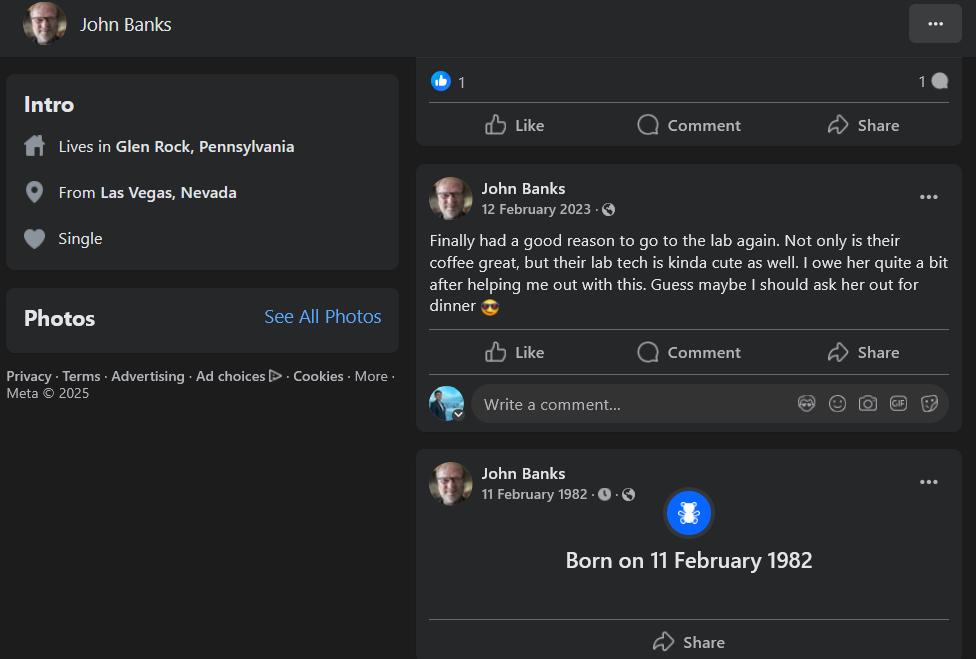
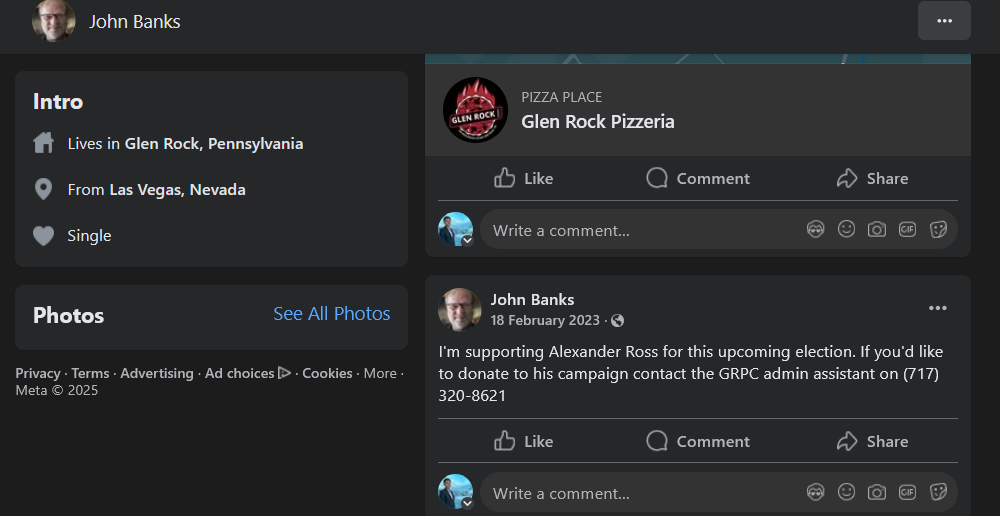
Answer:
Sm9obiBCYW5rcw==Q2: What year was he born?
MTk4Mg==Q3: Which City is John from?
TGFzIFZlZ2FzWe were informed that John was a security consultant at GRPC. We then received a tip off from George ( who i think is Alec’s boss?) providing information about a reddit post. We gain some new data points for pivoting.
<Phone Rings>
<voicemail picks up>
Hello, please leave your message after the tone...beep
<George Hammond>
Alec you better be dead or in prison because that's the only reason you shouldn't have answered my last 3 calls.
Whatever you are doing down there is starting to make some waves. Glen Rock legal reached out to me yesterday and asked if we planned
to publish anything, then they gently implied...or maybe not so gently that it wouldn't be a good idea. So keep going. I'll also send
over an image we found on a conspiracy forum about Glen Rock...seems interesting...might be a lead
<voicemail beeps>
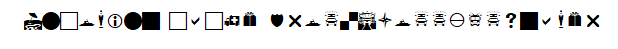
Q1: What is the name of the cache?
Started by trying to find out what exactly is the term for these “funky fonts”. Found that it is a category of fonts referred to as dingbat. Googled for a dingbat font translator and found dcode.fr which has a list of dingbat fonts. Scrolled through and the symbols seem to match the webdings font https://www.dcode.fr/webdings-font)
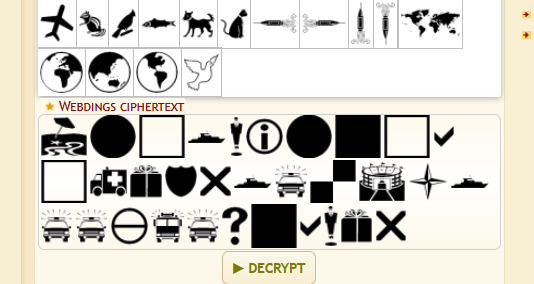
We get “Incoming cache drop.Sloppyfpsgamer” which shows one of the alias for John Banks.
Tried googling the term but no results. Had to check the hints as I am stumped. After doing some digging around, some letterboxing articles did mention geocaching which i guess is a modern implementation of letterboxing. Signed up for an account on geocaching.com and checked if there was a way to search for a user profile. Found our Sloppyfpsgamer profile on https://www.geocaching.com/p/?guid=fa4f8ca0-3e18-4844-b3c5-90885aeb2c82
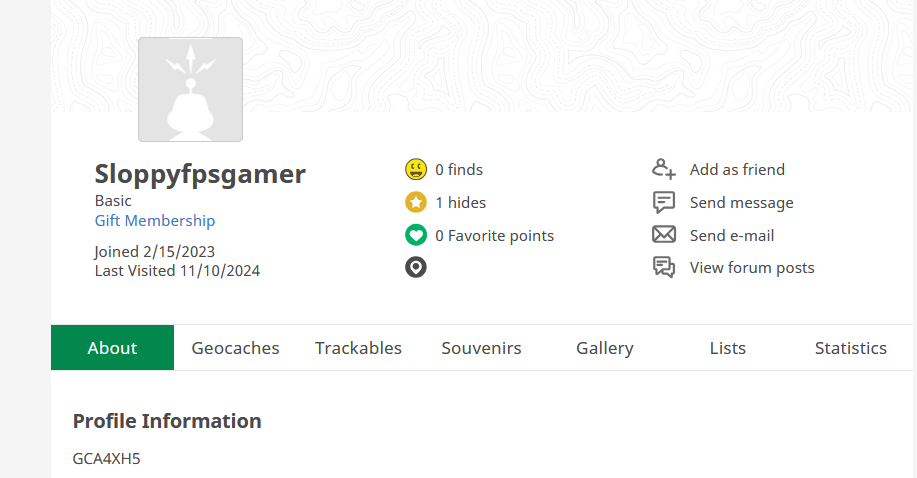
Interestingly when we go Geocaches, we see that the user had hidden a cache but it does not return no results. I then returned to the main profile page and well whatever the alphanumeric stuff is under the Profile Info looks suspicious as hell. So i took that and then search for it on geocache. Turns out it is what they called a GC and returns a valid result
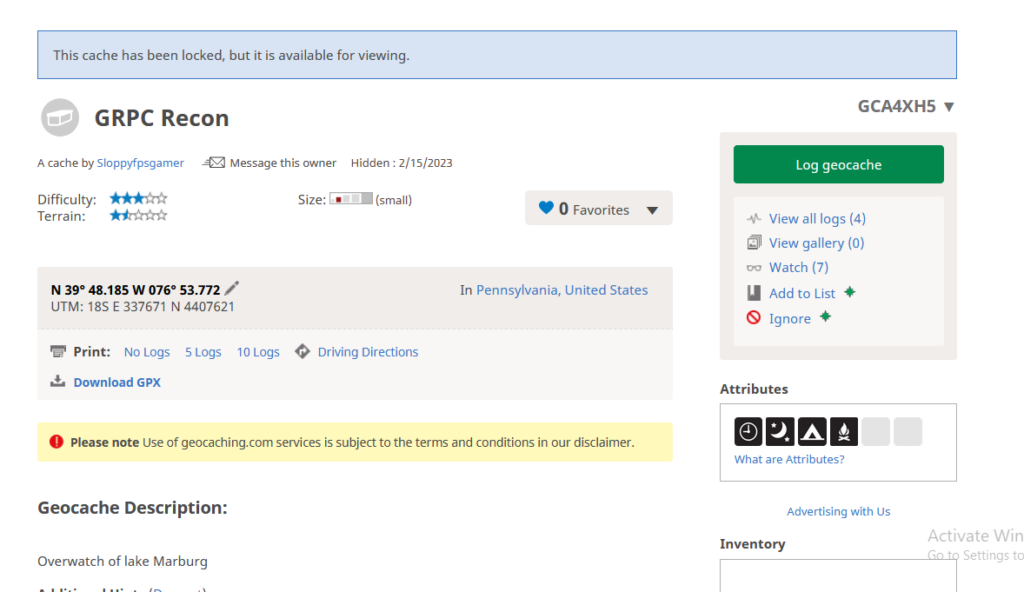
Answer
R1JQQyBSZWNvbg==Q2: Coordinates to the Cache
TiAzObAgNDguMTg1IFcgMDc2sCA1My43NzIgQ3: What did the encrypted text say that was posted on the conspiracy forum?
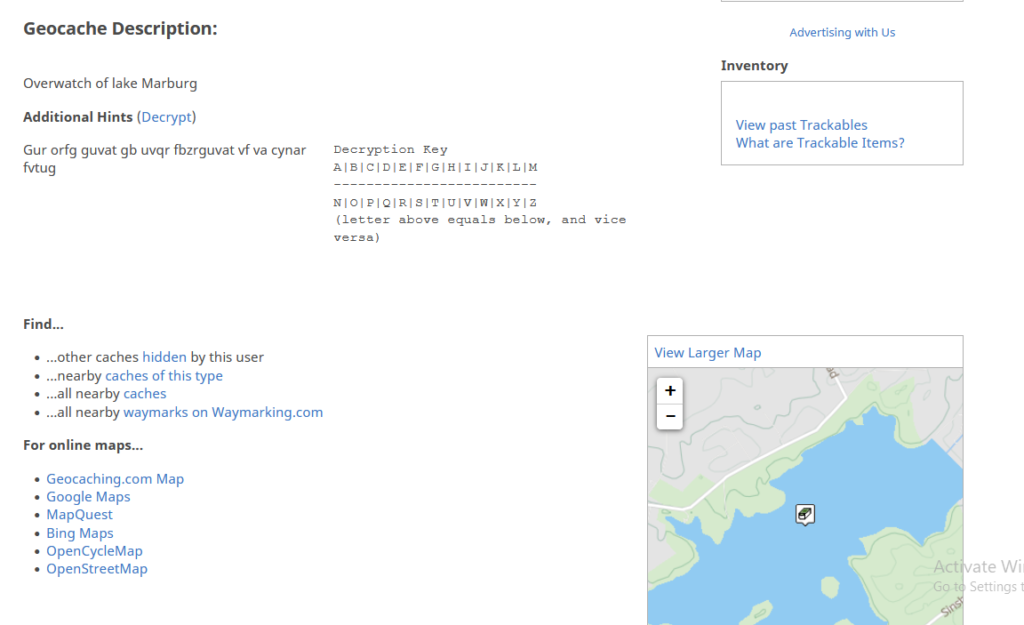
The message decrypts to “The best thing to hide something is in plane sight”. Plane might be a deliberate mis-spelling. We scroll further down to see something interesting including a user called “potatocat”
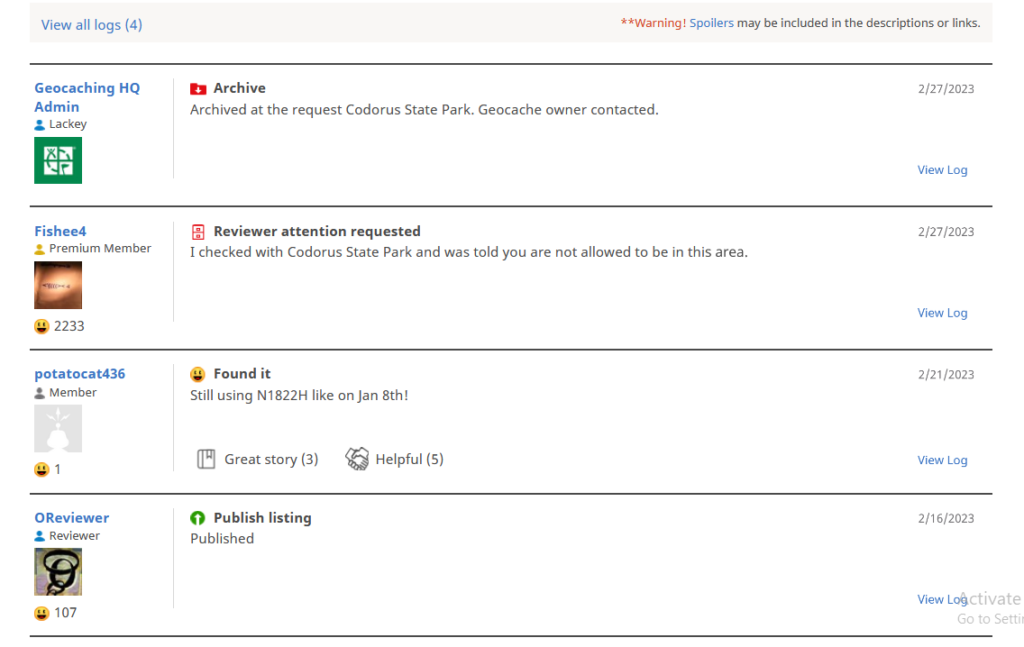
N1822H seems like plane’s tail number so I searched on google using the “tail number” as well as plane. So this was a rabbit hole and maybe i misinterpreted the question. The answer is the decrypted message from the webdings thingy
Answer
SW5jb21pbmcgY2FjaGUgZHJvcC5TbG9wcHlmcHNnYW1lcgo=So Alec went to the coordinates and picked up a cache

Q1: What does the text translate to?
First thought. This looks like a cipher. Maybe ROT 13 or caesar. Our previous dcode.fr should be useful to help us determine this.
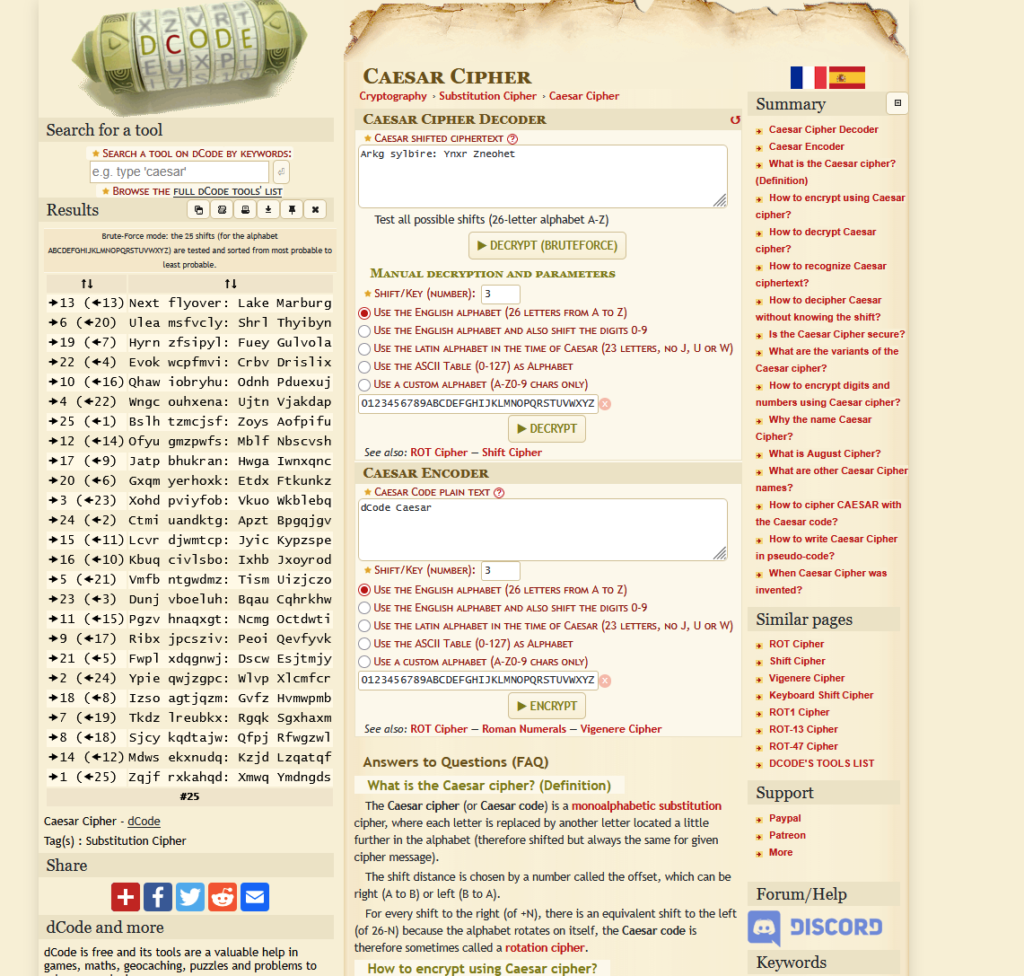
Looks like ROT 13. We then give 13 as the key.
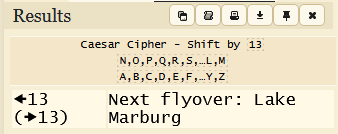
Answer:
TmV4dCBmbHlvdmVyOiBMYWtlIE1hcmJ1cmc=Q2: What does N1822H reference?
Well we already know what is this likely to be from the previous section:)
Answer
cGxhbmU=Q3: What type of aircraft is N1822H?
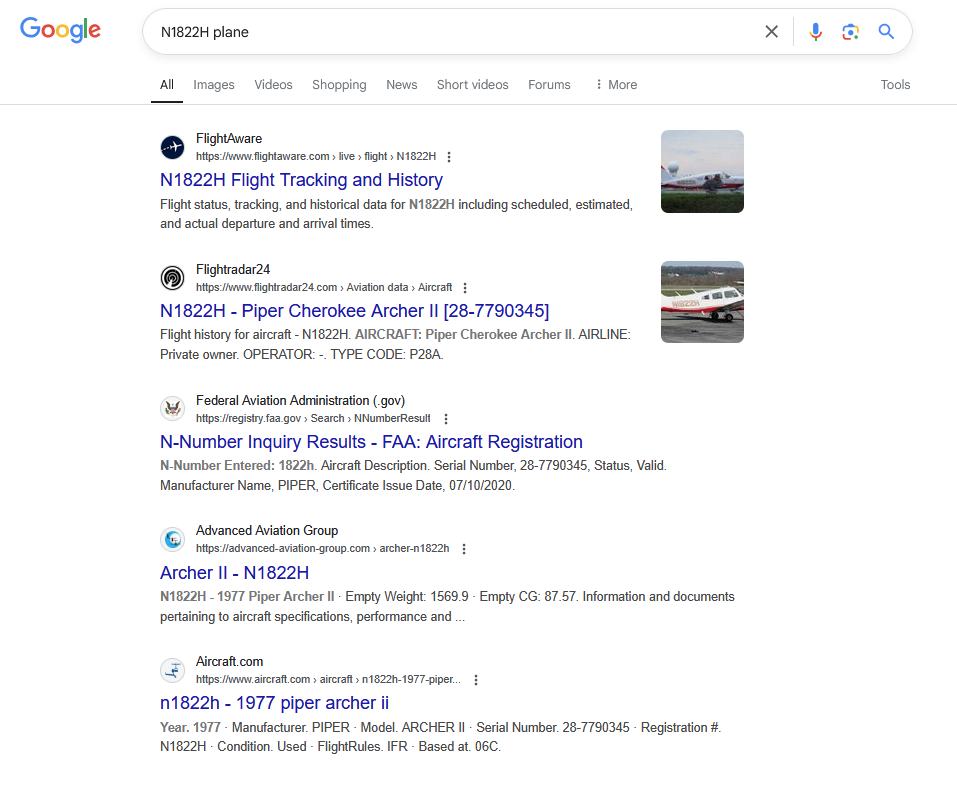
Plenty of options to choose from. Answer that worked for me:
UGlwZXIgQ2hlcm9rZWU=The bossman gave us some kml data from flightaware. With some searching, we find that we can use Google Earth to import the kml file. After importing the file, we are greeted with the presumed flight path of N1822h on the 8 Jan 2023.
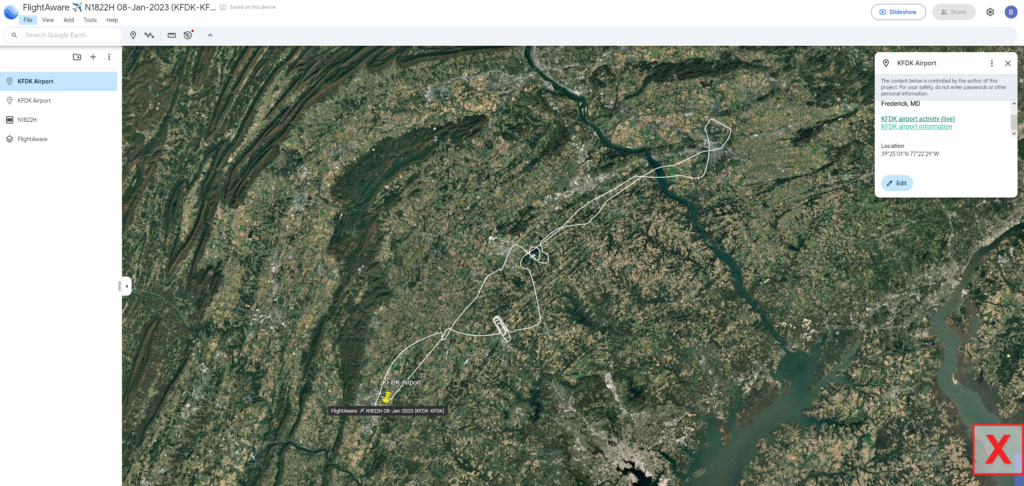
Q1:Which airport did this aircraft fly out of on January 8th 2023?
We can see that from Google Earth so straightforward answer.
Answer:
S0ZESyBBaXJwb3J0Q2: Which lake did the plane fly over on January the 8th?
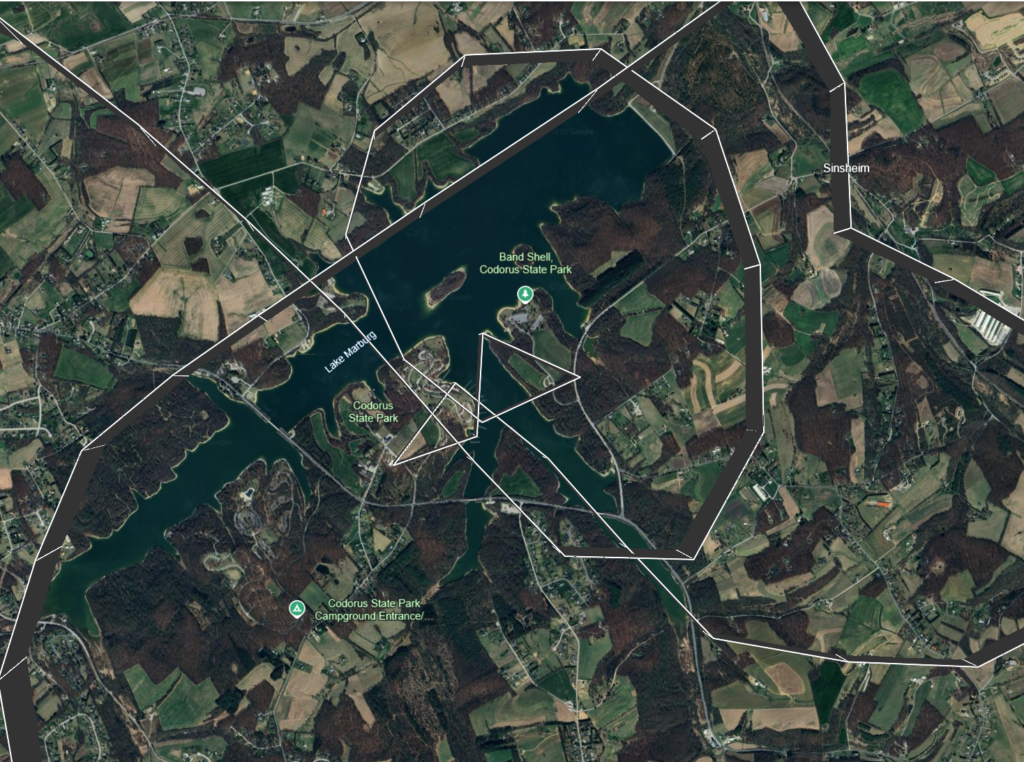
Answer:
TGFrZSBNYXJidXJnWe received a threat from a rather familiar looking phone number (LOL OPSEC). Thanks to the power of maltego, before even starting the section, i think we know who the number belonged to.
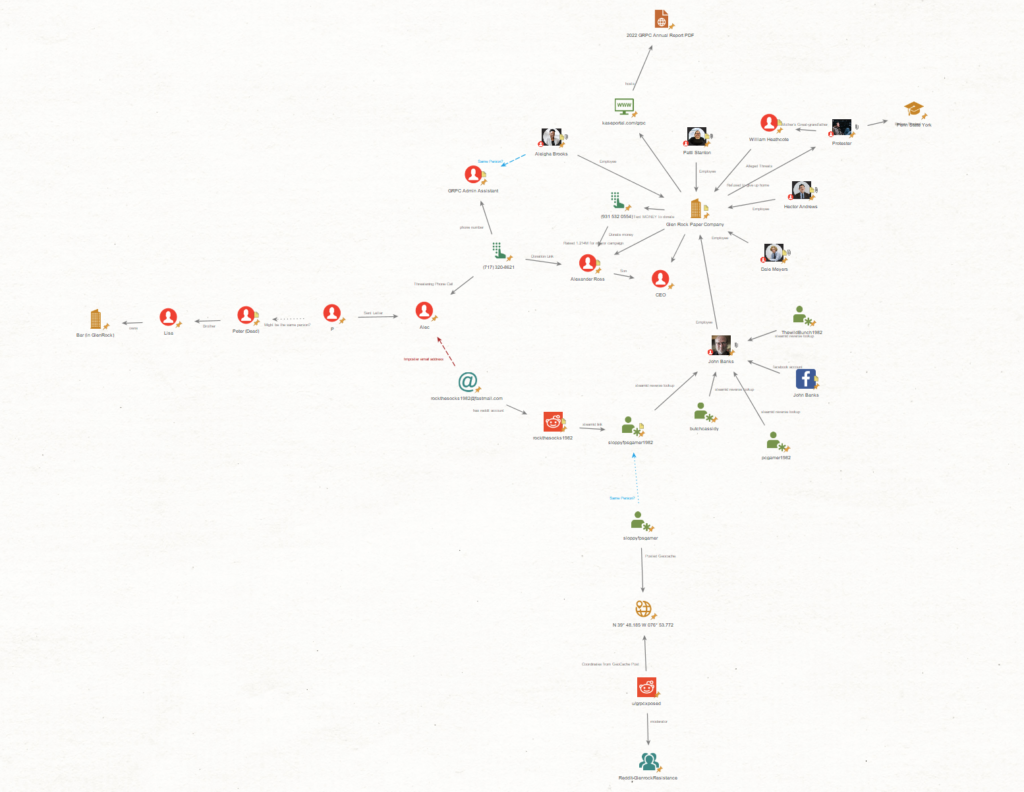
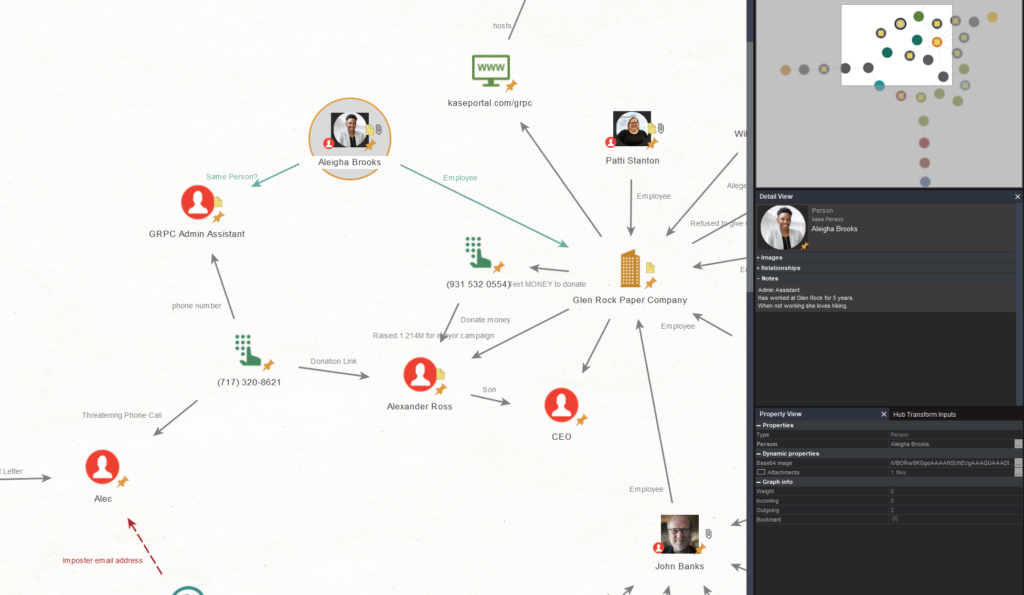
Q1: Who is the owner of the phone number?
Answer
QWxlaWdoYSBCcm9va3M=The lab results are back and they are BAD.
Lisa sent us a voicemail and told us that a certain picture has the answer. There is a scribble at the back of the photo. A potential username or alias:

Q1: 0x
The hell? Ok this is likely to be something to do with hexadecimal with the 0x. So we downloaded both photos and see what we can do with them. Maybe steganography who knows.
Lets search the interweb first for the username. We find a post on Badger & Blade with that username, from Pennsylvania, and ocean scented (boat?). Not much clues other than this but maybe this is linked. Has an alias “R”.
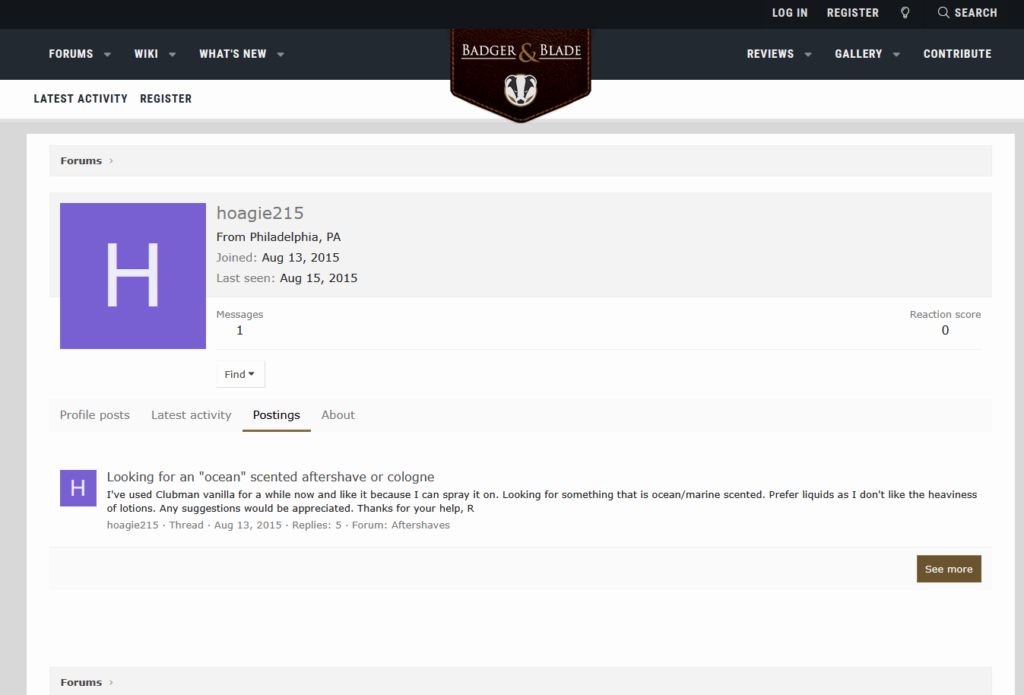
However I think this is probably a coincidence and belongs to this guy instead who is probably not linked to the scenario
Nothing with the Steganography end as well. Ran strings and exiftool. Nothing too exciting. Maybe lets see if i can reverse image search that weird boat logo.
I just get a bunch of results that dont match the actual ship itself. Even used Yandex Image search.
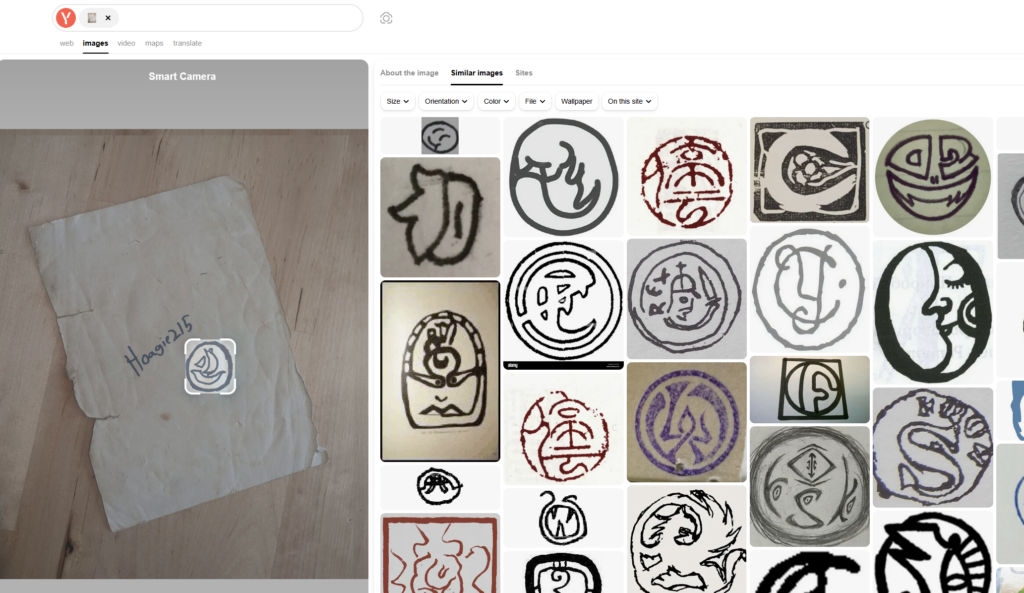
Used the hint and after screwing around for a while, apparently adding an open sea search term together with the picture shows a similar logo. Looks like a crypto market?
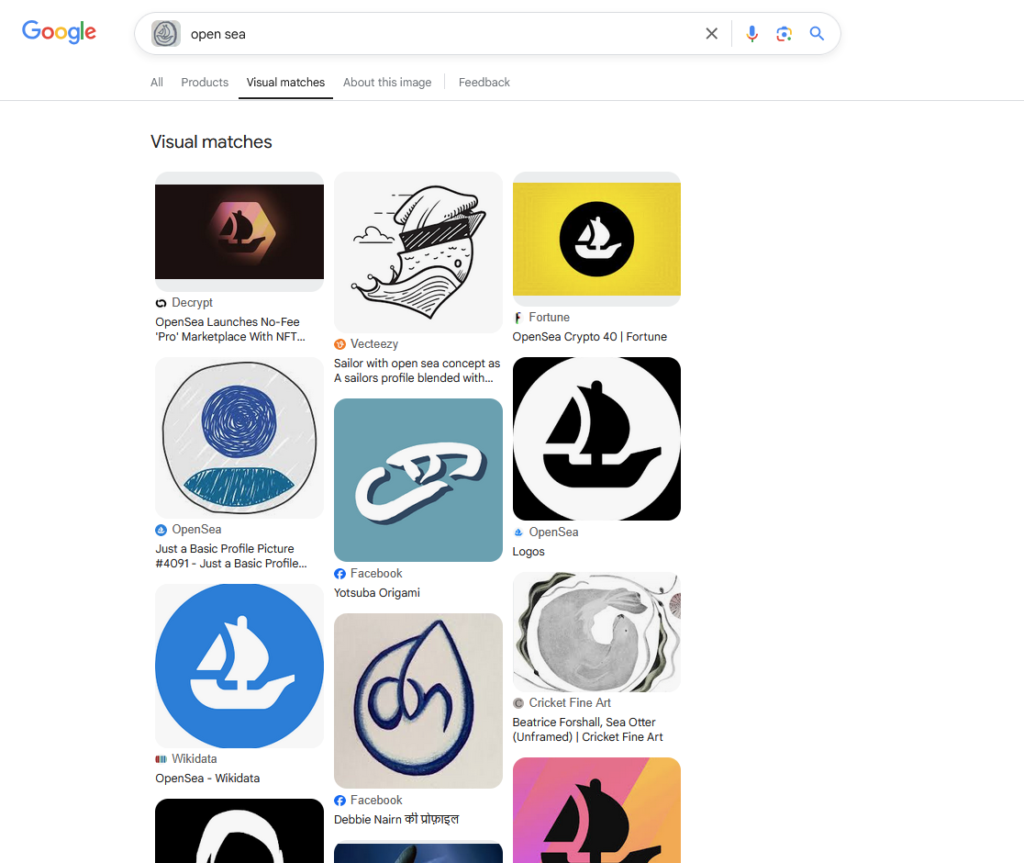
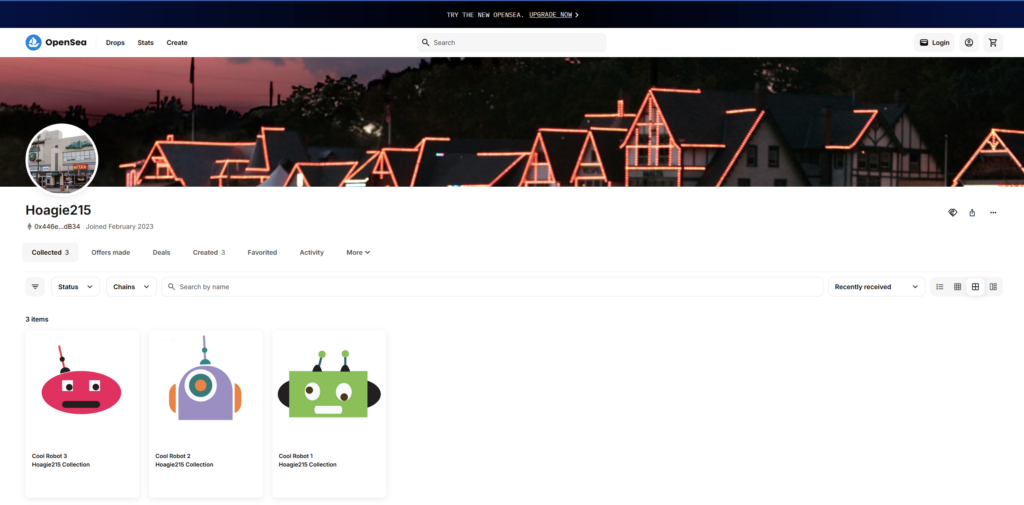
So there is an account of that username Hoagie215 and the crypto address i presume right below the name. This WAS REALLY TRICKY
Answer:
MHg0NDZlRUI0ODA1MTZCNzgyNEM0RDkzODc0MEE1YTQxMENBMGNkQjM0Q2: Image 1
erm nani? Presumably the Cool Robot 1 image? I keyed in that name but i got a big fat wrong. The hint was like LOOK CLOSER. Hmm okay Lets zoom in on the picture and you do see something which was the answer. But this was kinda unclear man…. (I feel this was kinda er lazy?)
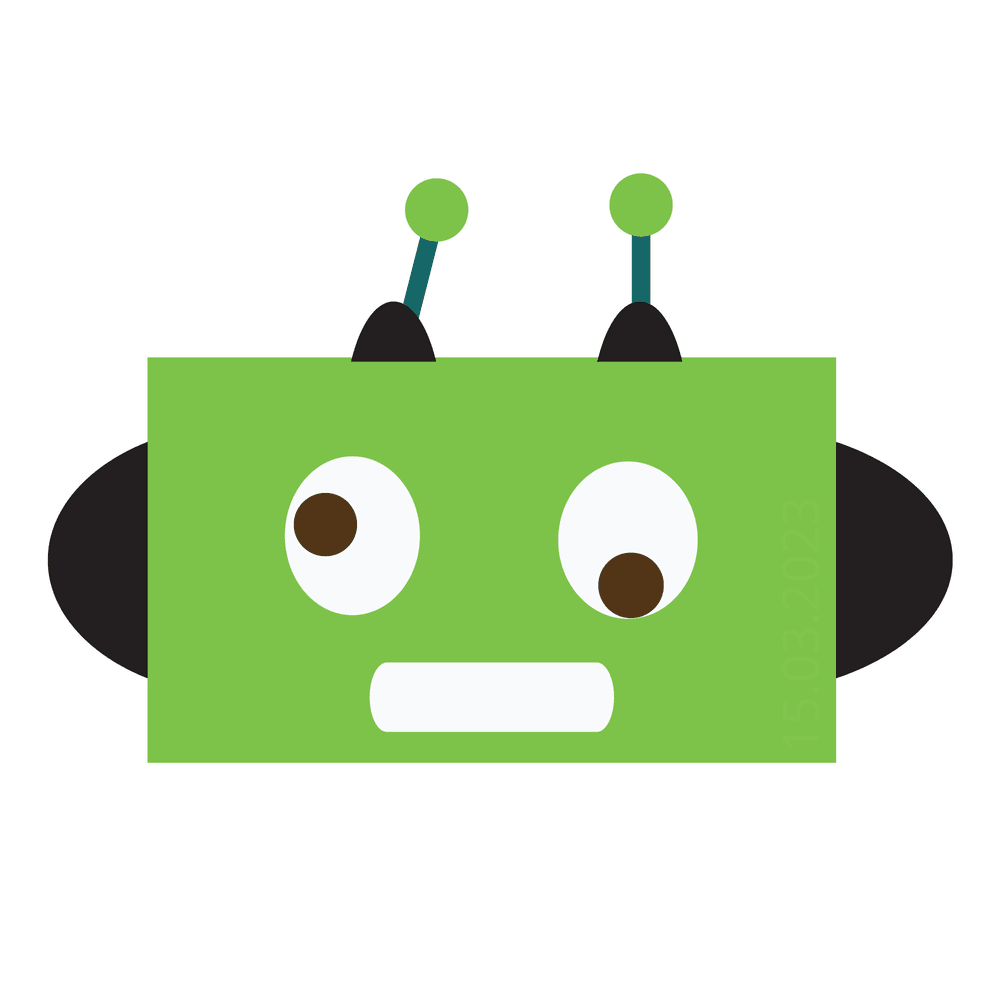
Answer:
MTUuMDMuMjAyMw==Q3:Image 2
Oh no what on earth am i supposed to find out here. Zooming in doesn’t quite reveal anything though there are two lightly shaded grey dots at one corner. I googled for image osint ctf tools and came across this github repo (https://github.com/s0v1x/CTF-tools). One of the tools (https://29a.ch/photo-forensics/#forensic-magnifier) was able to give me the answer. I learnt something new with this tool.
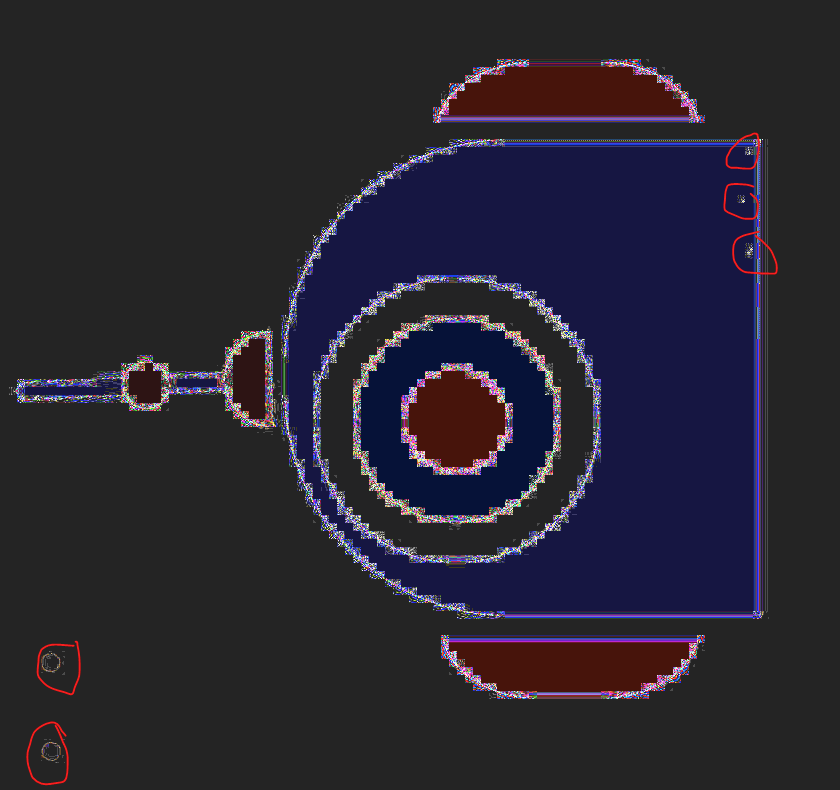
Hm apparently I needed to downloaded the image directly (as a avif file) instead of snipshot which results in data loss. Once i uploaded the avif file instead, it became clear.
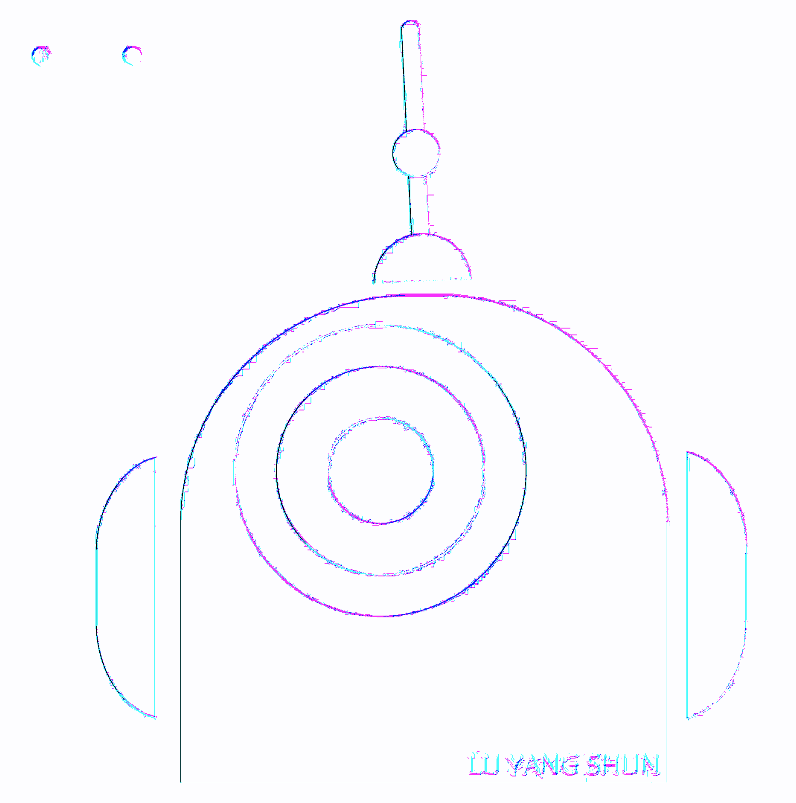
Answer
TFUgWUFORyBTSFVOQ3: Image 3
Haiz what trick could this be. Same tool. We see what appears to be coordinates?
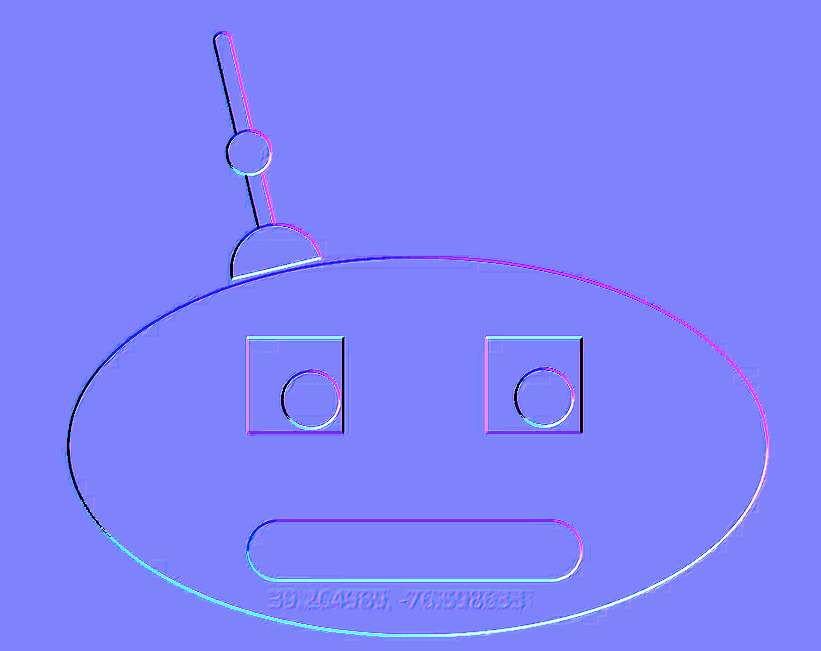
Wasnt sure if some of the digits were 6 or 8 so there was a bit of trial and error until one fit. Coordinates point to Baltimore Harbor and we are even given additional info (The password for the pivot chart is: muddywater)
Answer:
MzkuMjY0OTY5LCAtNzYuNTk4NjMzWe are told that GRPC has been receiving chemicals via the ship LU YANG SHUN from Baltimore Port. Oh actually the game is over and the rest of it is just narrative from now on.
Feels a bit anti-climatic though:( But I did learn some cool tricks. Looking forward to the other scenario i purchased!
My maltego graph for download if you want to play around with it!
https://drive.google.com/file/d/1npDHqL0ElIMdn0EXppvumkxZSK8tV3M1/view?usp=sharing